Someone recently managed to get on a Microsoft Teams call with representatives from phone hacking company Cellebrite, and then leaked a screenshot of the company’s capabilities against many Google Pixel phones, according to a forum post about the leak and 404 Media’s review of the material.
The leak follows others obtained and verified by 404 Media over the last 18 months. Those leaks impacted both Cellebrite and its competitor Grayshift, now owned by Magnet Forensics. Both companies constantly hunt for techniques to unlock phones law enforcement have physical access to.
“You can Teams meeting with them. They tell everything. Still cannot extract esim on Pixel. Ask anything,” a user called rogueFed wrote on the GrapheneOS forum on Wednesday, speaking about what they learned about Cellebrite capabilities. GrapheneOS is a security- and privacy-focused Android-based operating system.
rogueFed then posted two screenshots of the Microsoft Teams call. The first was a Cellebrite Support Matrix, which lays out whether the company’s tech can, or can’t, unlock certain phones and under what conditions. The second screenshot was of a Cellebrite employee.
💡
Do you know anything else about phone unlocking technology? I would love to hear from you. Using a non-work device, you can message me securely on Signal at joseph.404 or send me an email at joseph@404media.co.According to another of rogueFed’s posts, the meeting took place in October. The meeting appears to have been a sales call. The employee is a “pre sales expert,” according to a profile available online.
The Support Matrix is focused on modern Google Pixel devices, including the Pixel 9 series. The screenshot does not include details on the Pixel 10, which is Google’s latest device. It discusses Cellebrite’s capabilities regarding ‘before first unlock’, or BFU, when a piece of phone unlocking tech tries to open a device before someone has typed in the phone’s passcode for the first time since being turned on. It also shows Cellebrite’s capabilities against after first unlock, or AFU, devices.
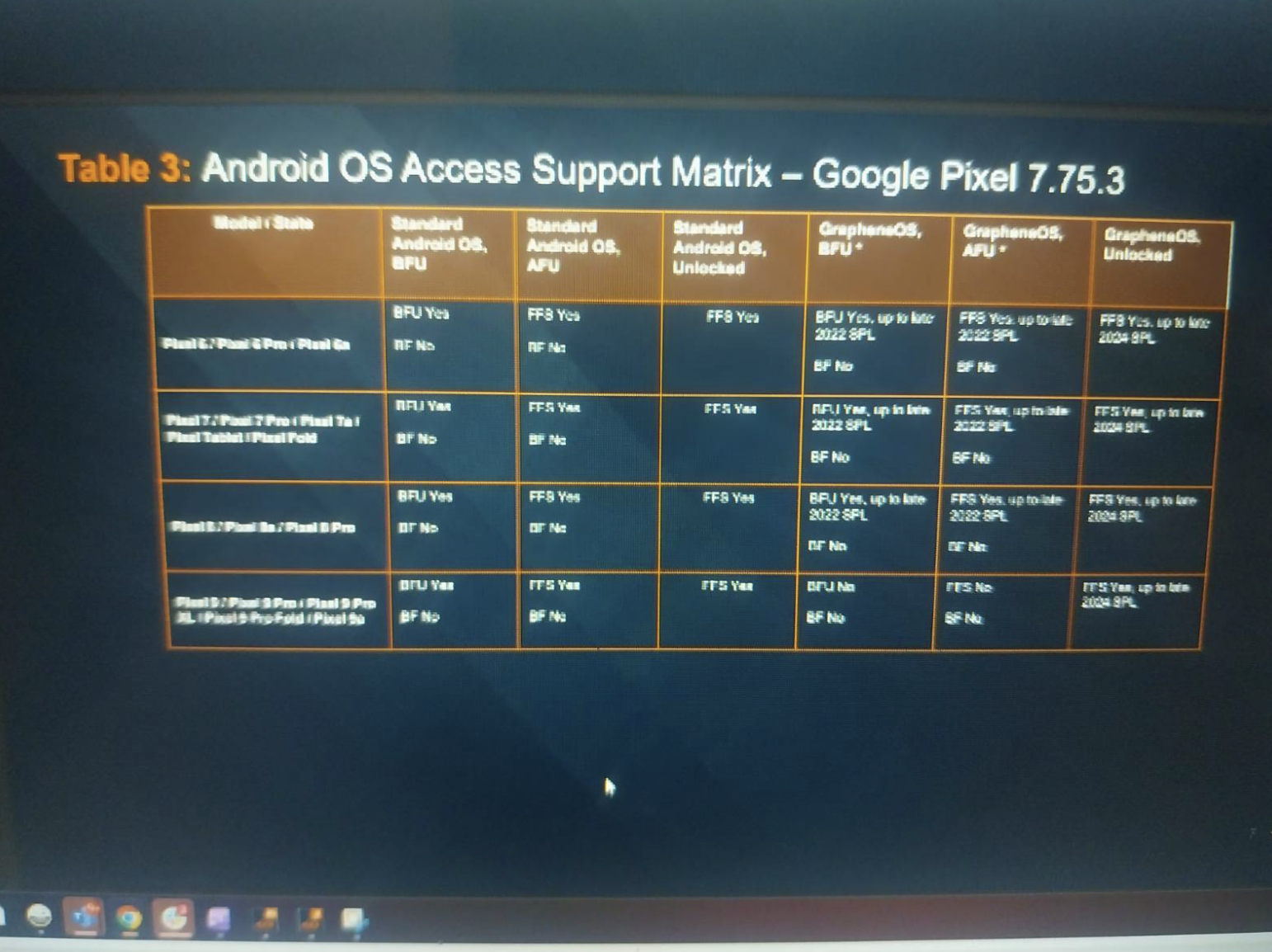
Screenshot via
GrapheneOS forum.
The Support Matrix also shows Cellebrite’s capabilities against Pixel devices running GrapheneOS, with some differences between phones running that operating system and stock Android. Cellebrite does support, for example, Pixel 9 devices BFU. Meanwhile the screenshot indicates Cellebrite cannot unlock Pixel 9 devices running GrapheneOS BFU.
In a statement, Victor Cooper, senior director of corporate communications and content strategy at Cellebrite, told 404 Media “We do not disclose or publicize the specific capabilities of our technology. This practice is central to our security strategy, as revealing such details could provide potential criminals or malicious actors with an unintended advantage.” Google did not immediately respond to a request for comment.
GrapheneOS is a long running project which makes sizable security changes to an Android device. “GrapheneOS is focused on substance rather than branding and marketing. It doesn't take the typical approach of piling on a bunch of insecure features depending on the adversaries not knowing about them and regressing actual privacy/security. It's a very technical project building privacy and security into the OS rather than including assorted unhelpful frills or bundling subjective third party apps choices,” the project’s website reads.
As well as being used by the privacy and security conscious, criminals also turn to GrapheneOS. After the FBI secretly ran its own backdoored encrypted phone company for criminals, some drug traffickers and the people who sell technology to the underworld shifted to using GrapheneOS devices with Signal installed, according to interviews with phone sellers.
In their forum post, rogueFed wrote that the “meeting focused specific on GrapheneOS bypass capability.”
They added “very fresh info more coming.”
 undefined Oblomov shared this topic
undefined Oblomov shared this topic



 Screenshot via
Screenshot via