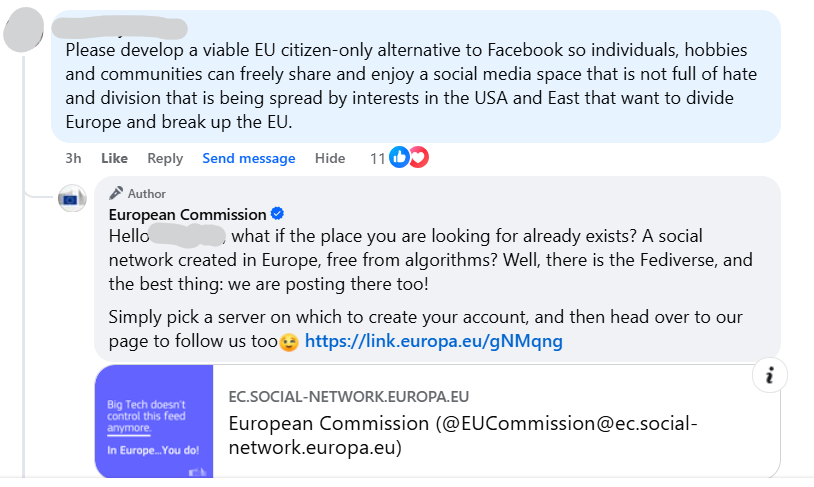
Today, Project Zero released a 0-click exploit chain for the Pixel 9.
-
We hope this flag makes it out of Clang experimental, and more vendors start using it!
@natashenka That feels a lot like Microsoft's SAL: https://learn.microsoft.com/en-us/cpp/code-quality/using-sal-annotations-to-reduce-c-cpp-code-defects?view=msvc-170. The big question is, how do we ensure portability to multiple compilers. Could we standardize that, please?
-
Today, Project Zero released a 0-click exploit chain for the Pixel 9. While it targets the Pixel, the 0-click bug and exploit techniques we used apply to most other Android devices.
https://projectzero.google/2026/01/pixel-0-click-part-1.html
-
Attack surface reduction is also important— the UDC is largely used by commercial media like TV shows, most devices don’t even have an encoder.
Does it really need to be 0-click?
@natashenka I don't know that a single click matters, unless you design it well. See also https://infosec.exchange/@adamshostack/115884932482637376
-
@natashenka wait, it transcribes them *by default* in the background? if so, that is an absolutely ridiculous attack surface to expose.
@gsuberland @natashenka IIRC that was already the case with Stagefright, which was also very similar in that it targeted media libraries involved in MMS
-
Today, Project Zero released a 0-click exploit chain for the Pixel 9. While it targets the Pixel, the 0-click bug and exploit techniques we used apply to most other Android devices.
https://projectzero.google/2026/01/pixel-0-click-part-1.html
@natashenka using of #grapheneos on our pixel phone is a workaround / solution - right? 🤔😉
-
Today, Project Zero released a 0-click exploit chain for the Pixel 9. While it targets the Pixel, the 0-click bug and exploit techniques we used apply to most other Android devices.
https://projectzero.google/2026/01/pixel-0-click-part-1.html
@GrapheneOS Would this exploit have been possible on GrapheneOS?
-
Today, Project Zero released a 0-click exploit chain for the Pixel 9. While it targets the Pixel, the 0-click bug and exploit techniques we used apply to most other Android devices.
https://projectzero.google/2026/01/pixel-0-click-part-1.html
@natashenka breaking out of the decoder is cooked, but I guess this one doesn't integrate into the hardware that much? or does it
-
@GrapheneOS Would this exploit have been possible on GrapheneOS?
-
Today, Project Zero released a 0-click exploit chain for the Pixel 9. While it targets the Pixel, the 0-click bug and exploit techniques we used apply to most other Android devices.
https://projectzero.google/2026/01/pixel-0-click-part-1.html
@natashenka a-bloody-mazing ! Thanks for the hard work
-
Today, Project Zero released a 0-click exploit chain for the Pixel 9. While it targets the Pixel, the 0-click bug and exploit techniques we used apply to most other Android devices.
https://projectzero.google/2026/01/pixel-0-click-part-1.html
@natashenka@infosec.exchange Does it apply to other sms apps on a Pixel?
-
 undefined oblomov@sociale.network shared this topic on
undefined oblomov@sociale.network shared this topic on