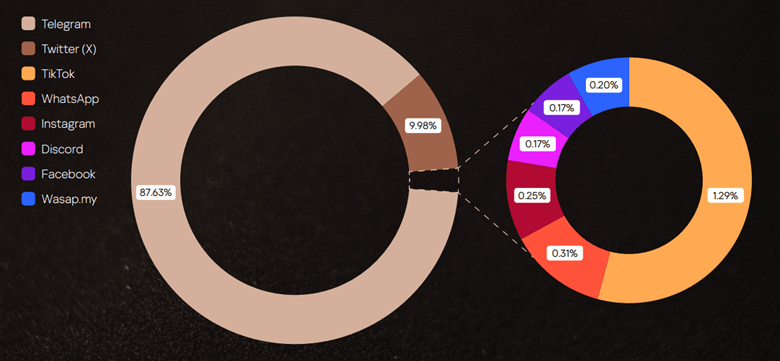
Signal in the noise: what hashtags reveal about hacktivism in 2025What do hacktivist campaigns look like in 2025? To answer this question, we analyzed more than 11,000 posts produced by over 120 hacktivist groups circulating across both the surface web and the dark web, with a particular focus on groups targeting MENA countries. The primary goal of our research is to highlight patterns in hacktivist operations, including attack methods, public warnings, and stated intent. The analysis is undertaken exclusively from a cybersecurity perspective and anchored in the principle of neutrality.Hacktivists are politically motivated threat actors who typically value visibility over sophistication. Their tactics are designed for maximum visibility, reach, and ease of execution, rather than stealth or technical complexity. The term “hacktivist” may refer to either the administrator of a community who initiates the attack or an ordinary subscriber who simply participates in the campaign.Key findingsWhile it may be assumed that most operations unfold on hidden forums, in fact, most hacktivist planning and mobilization happens in the open. Telegram has become the command center for today’s hacktivist groups, hosting the highest density of attack planning and calls to action. The second place is occupied by X (ex-Twitter).Distribution of social media references in posts published in 2025Although we focused on hacktivists operating in MENA, the targeting of the groups under review is global, extending well beyond the region. There are victims throughout Europe and Middle East, as well as Argentina, the United States, Indonesia, India, Vietnam, Thailand, Cambodia, Türkiye, and others.Hashtags as the connective tissue of hacktivist operationsOne notable feature of hacktivist posts and messages on dark web sites is the frequent use of hashtags (#words). Used in their posts constantly, hashtags often serve as political slogans, amplifying messages, coordinating activity or claiming credit for attacks. The most common themes are political statements and hacktivist groups names, though hashtags sometimes reference geographical locations, such as specific countries or cities.Hashtags also map alliances and momentum. We have identified 2063 unique tags in 2025: 1484 appearing for the first time, and many tied directly to specific groups or joint campaigns. Most tags are short-lived, lasting about two months, with “popular” ones persisting longer when amplified by alliances; channel bans contribute to attrition.Operationally, reports of completed attacks dominate hashtagged content (58%), and within those, DDoS is the workhorse (61%). Spikes in threatening rhetoric do not by themselves predict more attacks, but timing matters: when threats are published, they typically refer to actions in the near term, i.e. the same week or month, making early warning from open-channel monitoring materially useful.The full version of the report details the following findings:How long it typically takes for an attack to be reported after an initial threat postHow hashtags are used to coordinate attacks or claim creditPatterns across campaigns and regionsThe types of cyberattacks being promoted or celebratedPractical takeaways and recommendationsFor defenders and corporate leaders, we recommend the following:Prioritize scalable DDoS mitigation and proactive security measures.Treat public threats as short-horizon indicators rather than long-range forecasts.Invest in continuous monitoring across Telegram and related ecosystems to discover alliance announcements, threat posts, and cross-posted “proof” rapidly.Even organizations outside geopolitical conflict zones should assume exposure: hacktivist campaigns seek reach and spectacle, not narrow geography, and hashtags remain a practical lens for separating noise from signals that demand action.To download the full report, please fill in the form below. (function (w, d, u) { var s = d.createElement("script"); s.async = true; s.src = u + "?" + ((Date.now() / 180000) | 0); var h = d.getElementsByTagName("script")[0]; h.parentNode.insertBefore(s, h); })(window, document, "https://cdn.bitrix24.eu/b30707545/crm/form/loader_1808.js"); initBxFormValidator({ formId: "inline/1808/7dlezh", emailFieldName: "CONTACT_EMAIL", redirectUrl: "https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2025/10/13172551/Hacktivist_report-DFI-META.pdf", naturalFieldNames: ["CONTACT_UF_CRM_NODES"], lengthRestrictedFieldNames: { CONTACT_EMAIL: 250, CONTACT_POST: 128, CONTACT_NAME: 50, CONTACT_UF_CRM_COMPANY: 255, CONTACT_UF_CRM_COMPANY_TAX_ID: 50, CONTACT_UF_CRM_PRODUCT_INTEREST: 255, CONTACT_UF_CRM_FORM_QUESTION_2: 255, CONTACT_UF_CRM_FORM_QUESTION_3: 255, CONTACT_UF_CRM_FORM_QUESTION_5: 255, }, });securelist.com/dfi-meta-hackti…
 undefined stefano_zan@mastodon.uno shared this topic on
undefined stefano_zan@mastodon.uno shared this topic on