- Home
- Categories
- Uncategorized
- Current* conditions near Sandusky, OH:
Current* conditions near Sandusky, OH:
Gli ultimi otto messaggi ricevuti dalla Federazione
-
@mhoye apparently also true in politics. That Platner guy's still trying to run as a Democrat to be a Senator.
-
@Dunpiteog e quando facevi le cassette per te o da dare a qualcuno, con tante canzoni di autori diversi?
-
Niente carne, niente ossa, solo codice! Il primo presentatore AI arriva da Channel 4
📌 Link all'articolo : https://www.redhotcyber.com/post/niente-carne-niente-ossa-solo-codice-il-primo-presentatore-ai-arriva-da-channel-4/
#redhotcyber #hacking #cti #ai #online #it #cybercrime #cybersecurity #technology #news #cyberthreatintelligence #innovation #privacy
-
@tinturadiodio ha già scritto tutto @tommi , ma aggiungo un +1 di persona che ha un conto da banca etica e ci si trova bene
-
fox@social.hostnetwork.xyz ah! Yes.
Whatever happened to the original owner of relaylist anyway?
-
This Week in Security: Court Orders, GlassWorm, TARmageddon, and It was DNS
This week, a US federal court has ruled that NSO Group is no longer allowed to use Pegasus spyware against users of WhatsApp. And for their trouble, NSO was also fined $4 million. It’s unclear how much this ruling will actually change NSO’s behavior, as it intentionally stopped short of applying to foreign governments.
There may be an unexpected source of leverage the US courts can exert over NSO, with the news that American investors are acquiring the company. Among the requirements of the ruling is that NSO cannot reverse engineer WhatsApp code, cannot create new WhatsApp accounts, and must delete any existing WhatsApp code in their possession. Whether this actually happens remains to be seen.
Points On the Curve
Cryptography is hard. Your implementation can do everything right, and still have a weakness. This was demonstrated yet again in the Cloudflare CIRCL cryptography library. The issue here is a Diffie-Hellman scheme using the Curve4Q elliptic curve.Quick review: Diffie-Hellman is a technique where Bob and Alice can exchange public keys, and each combine the received public key with their own private key, and arrive at a shared secret. This can be accomplished on an elliptic curve by choosing a scalar value as a private key, and multiplying a standard generator point by that scalar to derive a new point on the curve, which serves as the public key. After the public key points are exchanged, Alice and Bob each multiply the received public point by their own secret scalar. Just like simple multiplication, this function is commutative, and results in the same answer for both.
There is a catch that can cause problems. Not every value is a valid point on the curve, and doing calculations on these invalid points can lead to unusual results. The danger here isn’t remote code execution (RCE), but leaking information about the private key when doing an invalid calculation using these invalid points.
The CIRCL library had a couple instances where invalid points could be used. There’s a quirk of deserializing FourQ points, that the x value can be interpreted two ways, essentially a positive or negative x. The CIRCL logic attempts to deserialize an incoming point in one way, and if that point is not actually on the curve, the value is inverted (technically “conjugated”), and the new point is accepted without testing. There were a few other similar cases where points weren’t being validated. These flaws were reported to Cloudflare and fixed earlier this year.
GlassWorm
We recently covered Shai Hulud, an npm worm that actively uploaded itself into other npm libraries when it found valid credentials on compromised computers. It was something of a sea change in the world of library security. Now a month later, we have GlassWorm, a vscode extension worm.GlassWorm combines several very sneaky techniques. When it injects code into an extension, that code is hidden with Unicode shenanigans, rendering in VSCode as blank lines. Once this malicious VSCode extension is loaded, it reaches out to some interesting Command and Control (C2) infrastructure: The Solana blockchain is used as a sort of bulletproof DNS, hosting a a C2 IP address. There’s a second, almost equally weird C2 mechanism: Hosting those IP addresses in entries on a public Google Calendar.
Once this malware is running, it harvests credentials, and if it gets a chance, injects itself in the code for other extensions and tries to publish. And it also turns the compromised machine into a “Zombi”, part of a botnet, but also working as a RAT (Remote Access Trojan). All told, it’s really nasty malware, and seems to indicate a shift towards these meta-worms that are intended to infiltrate Open Source software repositories.
Speaking of npm, GitHub has begun making security enhancements in response to the Shai Hulud worm. It looks like good changes, like the deprecation of classic access tokens, in favor of shorter lived, granular tokens. TOTP (Time based One Time Password) is going away as a second factor of authentication, in favor of passkeys and similar. And finally, npm is encouraging the use of doing away with long-lived access tokens altogether, and publishing strictly from CI/CD systems.
TARmageddon
We’ve cheered on the progress of the Rust language and its security wins, particularly in the realm of memory safety. But memory management is not the only cause of security issues. The async-tar rust package had a parsing bug that allowed a .tar file to smuggle additional contents that were not seen by the initial validation step.That has all sorts of potential security ramifications, like smuggling malicious files, bypassing filters, and more. But what’s really interesting about this particular bug is that it’s been around since the first release of the package, and async-tar has been forked into many other published packeges, some of which are in use but no longer maintained. This has turned what should have been a simple fix into a mess, and the popular tokio-tar is still unfixed.
It Was DNS
You probably noticed that the Internet was sort of a dumpster fire on Monday — more than normal. Most of the world, it seems, runs on Amazon’s AWS, and when AWS goes down, it’s surprising what else fails. There were the normal sites and services down, like Reddit, Signal, Fortnight, and Prime Video. It was a bit of a surprise that some banks were down and flights delayed. And then there were IoT devices, like smart beds, litter boxes, and smart bulbs.And the problem, naturally, was DNS. It’s always DNS. Specifically, Amazon has pinned the outage on “…a latent race condition in the DynamoDB DNS management system that resulted in an incorrect empty DNS record…”. This bad record brought down other services that relied on it, and it didn’t take long for the problem to spin out of control.
Bits and Bytes
There’s even more DNS, with [Dan Kaminsky]’s infamous cache poisoning making an unwelcome comeback. DNS has historically run over UDP, and the Kaminsky attack was based on the lack of authorization in DNS responses. The solution was to randomize the port a request was sent from, requiring the matching response be delivered to the same port number. What’s new here is that the Pseudo Random Number Generator (PRNG) in BIND has a weakness, that could have allowed predicting those values.TP-Link’s Omada gateways had a pair of vulnerabilities that allowed for RCE. The more serious of the two didn’t require any authentication. Noword on whether this flaw was accessible from the WAN interface by default. Patched firmware is now available.
The better-auth library patched an issue early this month, that allowed the createApiKey endpoint to run without authRequired set true, simply by providing a valid user ID. This bug has been in the library ever since API keys were added to the project. The fix landed in 1.3.26.
And for bonus points, go check out the ZDI post on Pwn2Own Ireland, that just wrapped. There were lots of IoT hacks, including at least one instance of Doom running on a printer. Summoning Team took the Master of Pwn award, nearly doubling the points earned by second place. Congrats!
-
Kind reminder (per chi se lo fosse perso)
Arriva anche il phastidioso Substack https://phastidio.net/2025/10/07/arriva-anche-il-phastidioso-substack/
-
@ilmondopositivo Mi sono praticamente strozzata a vedere "l'album più trash di sempre".
Mi sono trovata in una disavventura e Alex in pausa pranzo mi ha girato quella roba lì.
Post suggeriti
-
Niente carne, niente ossa, solo codice!
Watching Ignoring Scheduled Pinned Locked Moved Uncategorized redhotcyber hacking cti online cybercrime cybersecurity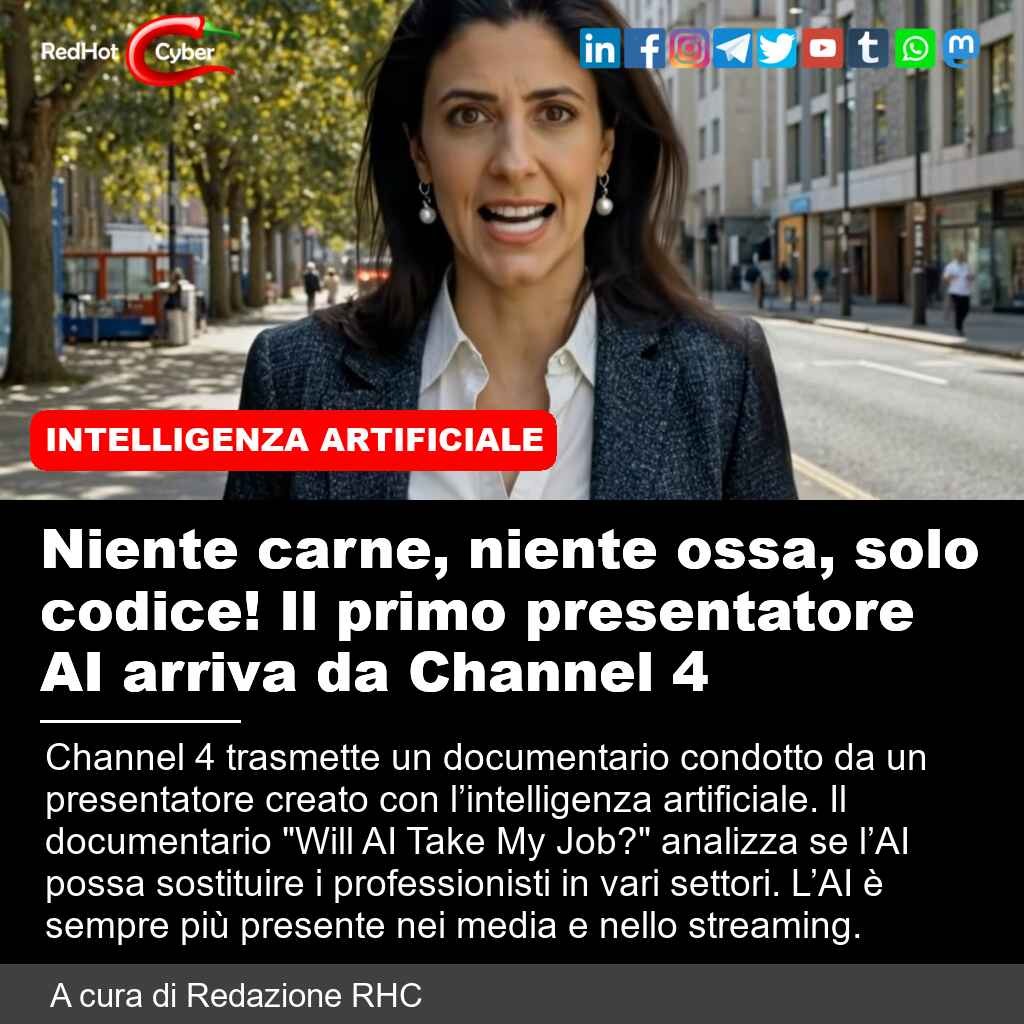 1
0 Votes1 Posts0 Views
1
0 Votes1 Posts0 Views -
Kind reminder (per chi se lo fosse perso)
Watching Ignoring Scheduled Pinned Locked Moved Uncategorized0 Votes1 Posts0 Views -
La posta del culo: contagiare di speranza
Watching Ignoring Scheduled Pinned Locked Moved Uncategorized esperienze musica0 Votes2 Posts0 Views -
@nilocram @informapirata @maupao @devol più o meno uguale qui
Watching Ignoring Scheduled Pinned Locked Moved Uncategorized0 Votes6 Posts0 Views
