My hard work has paid off!
Uncategorized
1
Posts
1
Posters
17
Views
-
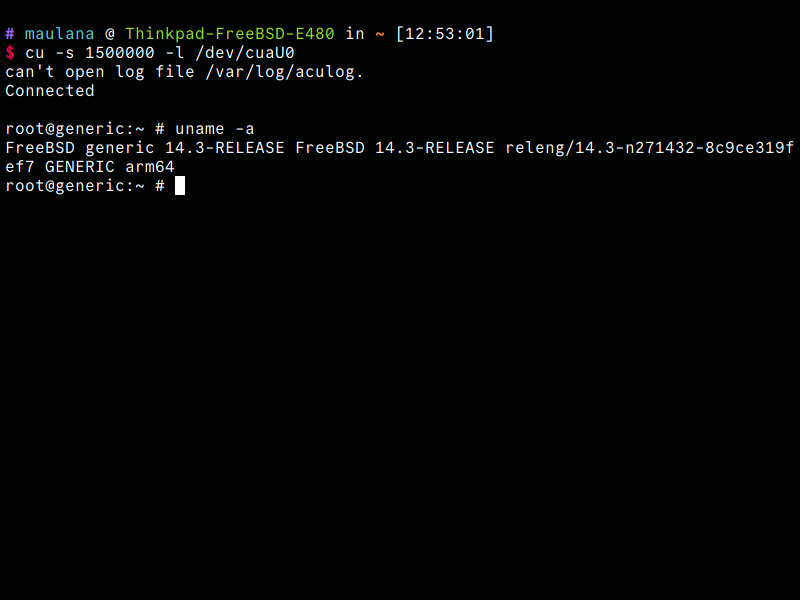
My hard work has paid off! I successfully booted FreeBSD on the NanoPi R2S Plus. FreeBSD automatically detected and resized the root filesystem, and I can now access it through the debug console.
My next challenge is creating a flashable image, since my current setup only works when I manually intervene during the boot process. Second problem, LAN port not detected due incorrect clock.
-
 undefined stefano@mastodon.bsd.cafe shared this topic on
undefined stefano@mastodon.bsd.cafe shared this topic on