Yet another (invalid) vulnerability report
Uncategorized
1
Posts
1
Posters
8
Views
-
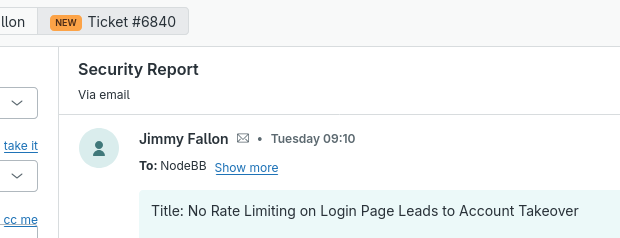
I had no idea Jimmy moonlighted as a pentester!
(The report is invalid, for those concerned, we've had rate limiting and account lockouts for years.)
-
 undefined nodebb@fosstodon.org shared this topic on
undefined nodebb@fosstodon.org shared this topic on